Network Support and Security | My Knowledge Check Full 100% 2023
“Network Support and Security | My Knowledge Check” will be randomly selected 20 questions from all chapters and the final exam, so it may vary from the below questions pool. To find all questions, you should use the search box at the top of header. Here are every day updated questions and answers.
-
Which protocol is used by network management systems to collect data from network devices?
- SNMP
- SMTP
- RDP
- TFTP
-
Explanation & Hints:
-
Employees in an organization report that they cannot access the customer database on the main server. Further investigation reveals that the database file is now encrypted. Shortly afterward, the organization receives a threatening email demanding payment for the decryption of the database file.
What type of attack has the organization experienced?
- ransomware
- man-in-the-middle attack
- trojan horse
- DoS attack
-
Match the authentication method to description.
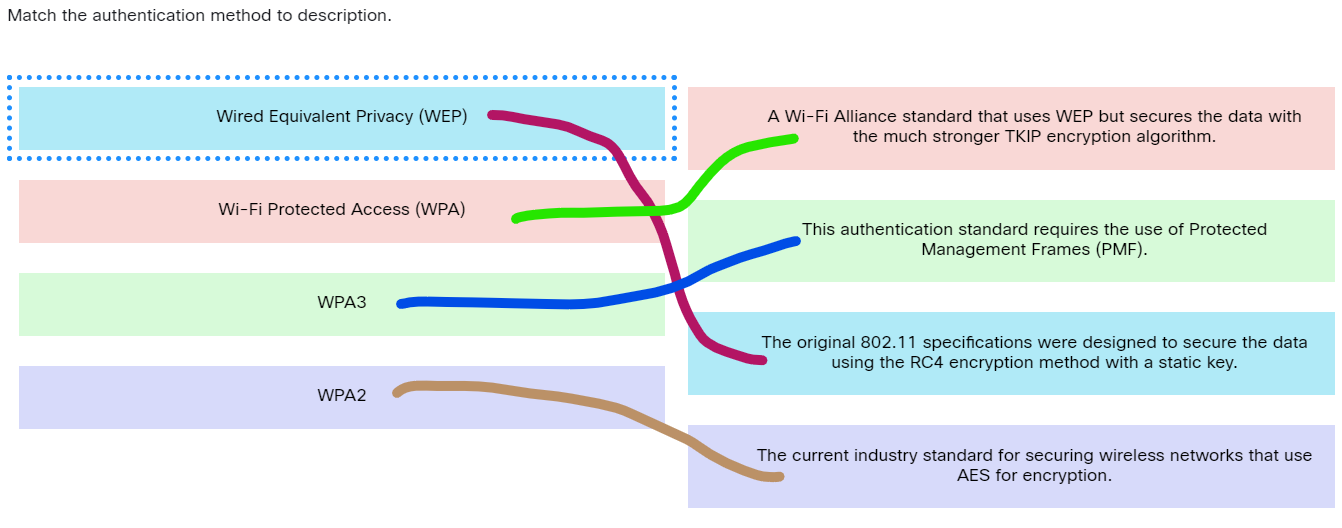
Match the authentication method to description. - Wired Equivalent Privacy (WEP) ==> The original 802.11 specifications were designed to secure the data using the RC4 encryption method with a static key.
- Wi-Fi Protected Access (WPA) ==> A Wi-Fi Alliance standard that uses WEP but secures the data with the much stronger TKIP encryption algorithm.
- WPA3 ==> This authentication standard requires the use of Protected Management Frames (PMF).
- WPA2 ==> The current industry standard for securing wireless networks that use AES for encryption.
-
Which output of a ping command can determine two important pieces of information? (Choose two.)
- whether or not the destination IP address is reachable through the network
- the round-trip time for the request to reach the destination and the response to return
- which network device is causing delays in delivering the packet to the destination IP address
- the number of domains that the packet travels through from the source to the destination
- the IP address of the gateway router that connects the source device to the internet
-
Match the examples of cyber threat to the description.
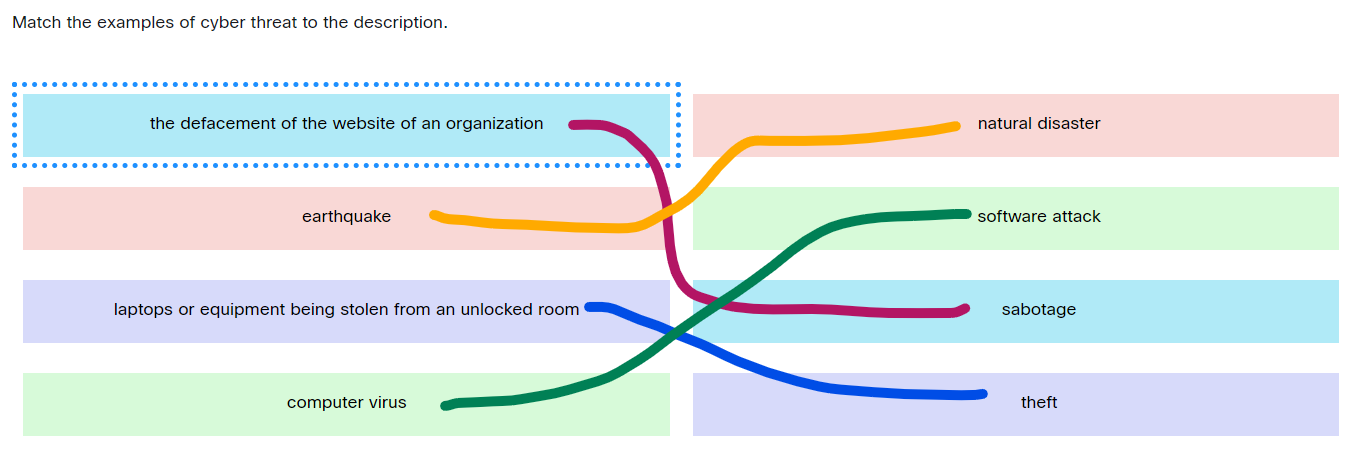
Match the examples of cyber threat to the description - the defacement of the website of an organization ==> sabotage
- earthquake ==> natural disaster
- laptops or equipment being stolen from an unlocked room ==> theft
- computer virus ==> software attack
-
Match the host-based security solution to the description.
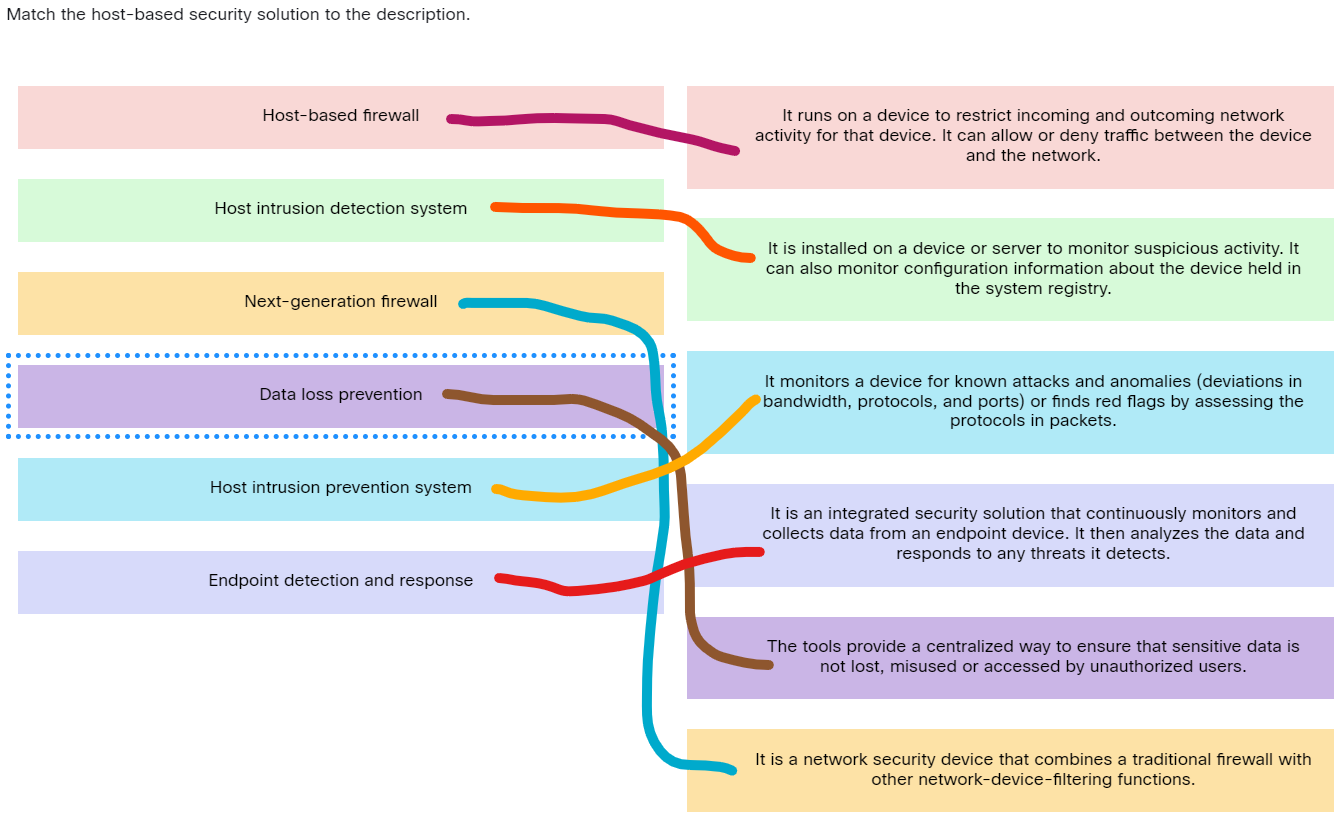
Match the host-based security solution to the description - Host-based firewall ==> It runs on a device to restrict incoming and outcoming network activity for that device. It can allow or deny traffic between the device and the network.
- Host intrusion detection system ==> It is installed on a device or server to monitor suspicious activity. It can also monitor configuration information about the device held in the system registry.
- Next-generation firewall ==> It is a network security device that combines a traditional firewall with other network-device-filtering functions.
- Data loss prevention ==> The tools provide a centralized way to ensure that sensitive data is not lost, misused or accessed by unauthorized users.
- Host intrusion prevention system ==> It monitors a device for known attacks and anomalies (deviations in bandwidth, protocols, and ports) or finds red flags by assessing the protocols in packets.
- Endpoint detection and response ==> It is an integrated security solution that continuously monitors and collects data from an endpoint device. It then analyzes the data and responds to any threats it detects.
-
Match the type of firewall to the description.
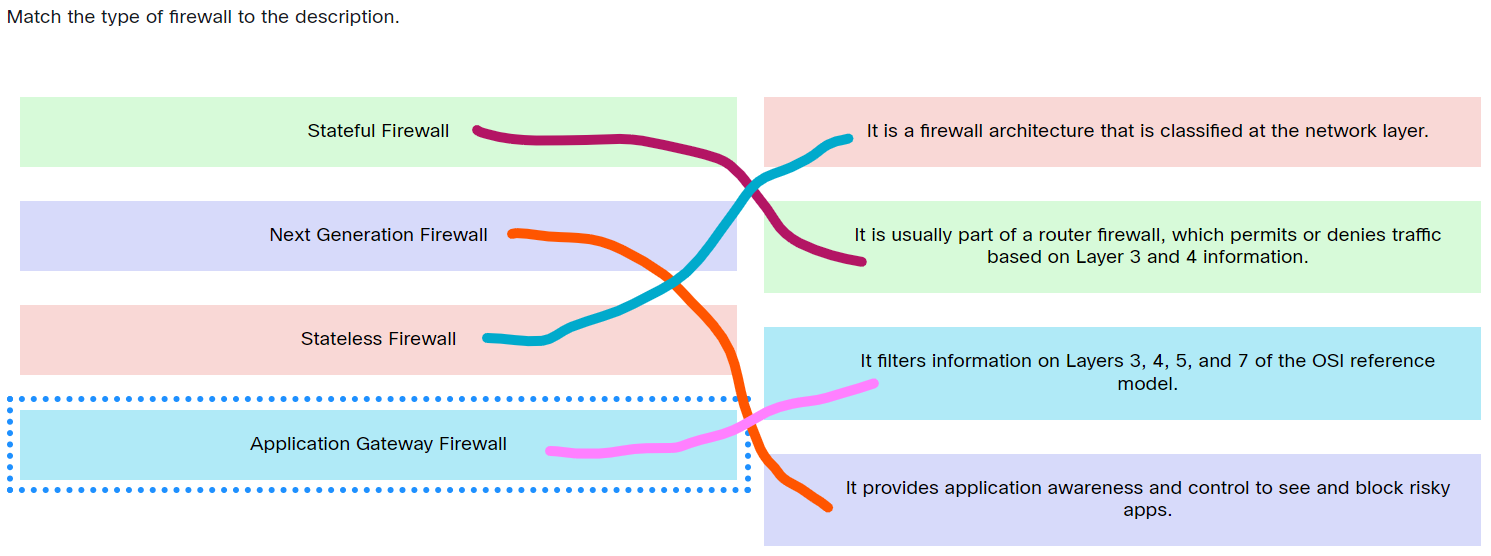
Match the type of firewall to the description. - Stateful Firewall ==> It is usually part of a router firewall, which permits or denies traffic based on Layer 3 and 4 information.
- Next Generation Firewall ==> It provides application awareness and control to see and block risky apps.
- Stateless Firewall ==> It is a firewall architecture that is classified at the network layer.
- Application Gateway Firewall ==> It filters information on Layers 3, 4, 5, and 7 of the OSI reference model.
-
A technician receives a trouble ticket from a user reporting that a website is no longer accessible. What two questions would the technician ask to narrow down the potential problem? (Choose two.)
- Could you access this web site previously from this device?
- Can you access other web sites from this computer browser?
- What model computer are you using to access this site?
- What operating system is installed on your computer?
- Do you remember your password to this web site?
-
A network technician troubleshoots a user’s PC problem and launches the Task Manager to gather more information. What information can the technician gather from the Task Manager output?
- the processes currently running on the PC
- the devices configured on the PC
- the errors that have occurred on the PC
- the drivers installed on the PC
-
An attacker is sitting in front of a store and wirelessly copies emails and contact lists from nearby unsuspecting user devices. What type of attack is this?
- bluesnarfing
- smishing
- RF jamming
- bluejacking
-
Which router IOS command displays the equivalent system information as many different show commands and is useful for troubleshooting a router?
- show tech-support
- show version
- show running-config
- show cdp neighbors detail
-
Which three solutions are examples of logical access control? (Choose three.)
- firewall
- access control list
- biometrics
- fence
- laptop lock
- swipe card
- firewall
-
Refer to the exhibit. A technician is attempting to map the local network using CDP. According to the output shown, which two statements are true about router Branch01?
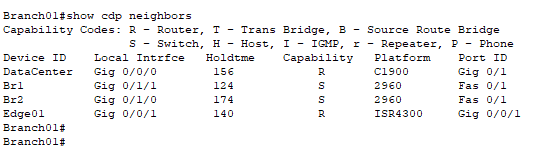
Network Support and Security Course Final Exam Answers 01 - Router Branch01 is directly connected to another router named DataCenter.
- Router Branch01 port Gi0/0/0 is directly connected to a Layer 2 switch
- Router Branch01 is directly connected to three Cisco switches.
- Router Branch01 is directly connected to port Fa0/1 on device BR1.
- Router Branch01 is directly connected to port Gi0/1/0 on device BR2.
-
Which security principle applies to the first dimension of the cybersecurity cube of the CIA triad?
- Accountability
- Availability
- Policy
- Technology
-
What three best practices can help defend against social engineering attacks? (Choose three.)
- Deploy well-designed firewall appliances.
- Educate employees regarding policies.
- Add more security guards.
- Do not provide password resets in a chat window.
- Enable a policy that states that the IT department should supply information over the phone only to managers.
- Resist the urge to click on enticing web links.
-
An administrator wishes to create a security policy document for end-users to protect against known unsafe websites and to warn the user about the dangers and handling of suspicious emails. What type of malware attack is being prevented?
- phishing
- adware protection
- trusted/untrusted sources verification
- DDoS
-
What are the two characteristics of a site-to-site VPN? (Choose two.)
- Clients have no awareness of the VPN.
- A VPN gateway device is needed at both ends of the tunnel.
- The client initiates the VPN connection.
- The VPN is established between the client PC and a VPN gateway.
- Traffic between clients and the VPN gateway is automatically encrypted.
-
A cyber criminal sends a series of maliciously formatted packets to the database server. The server cannot parse the packets and the event causes the server to crash. What is the type of attack the cyber criminal launches?
- packet Injection
- SQL injection
- DoS
- man-in-the-middle
-
Which authentication method uses AES for encryption?
- WEP
- WPA
- WPA2
- WPA3-Enterprise
-
What type of attack targets an SQL database using the input field of a user?
- XML injection
- Cross-site scripting
- SQL injection
- buffer overflow
Subscribe
Login
0 Comments
Oldest